Drive collaboration across suppliers and vendors by seamlessly sharing versioned designs with them. Receive documents and DFM in a centralized portal
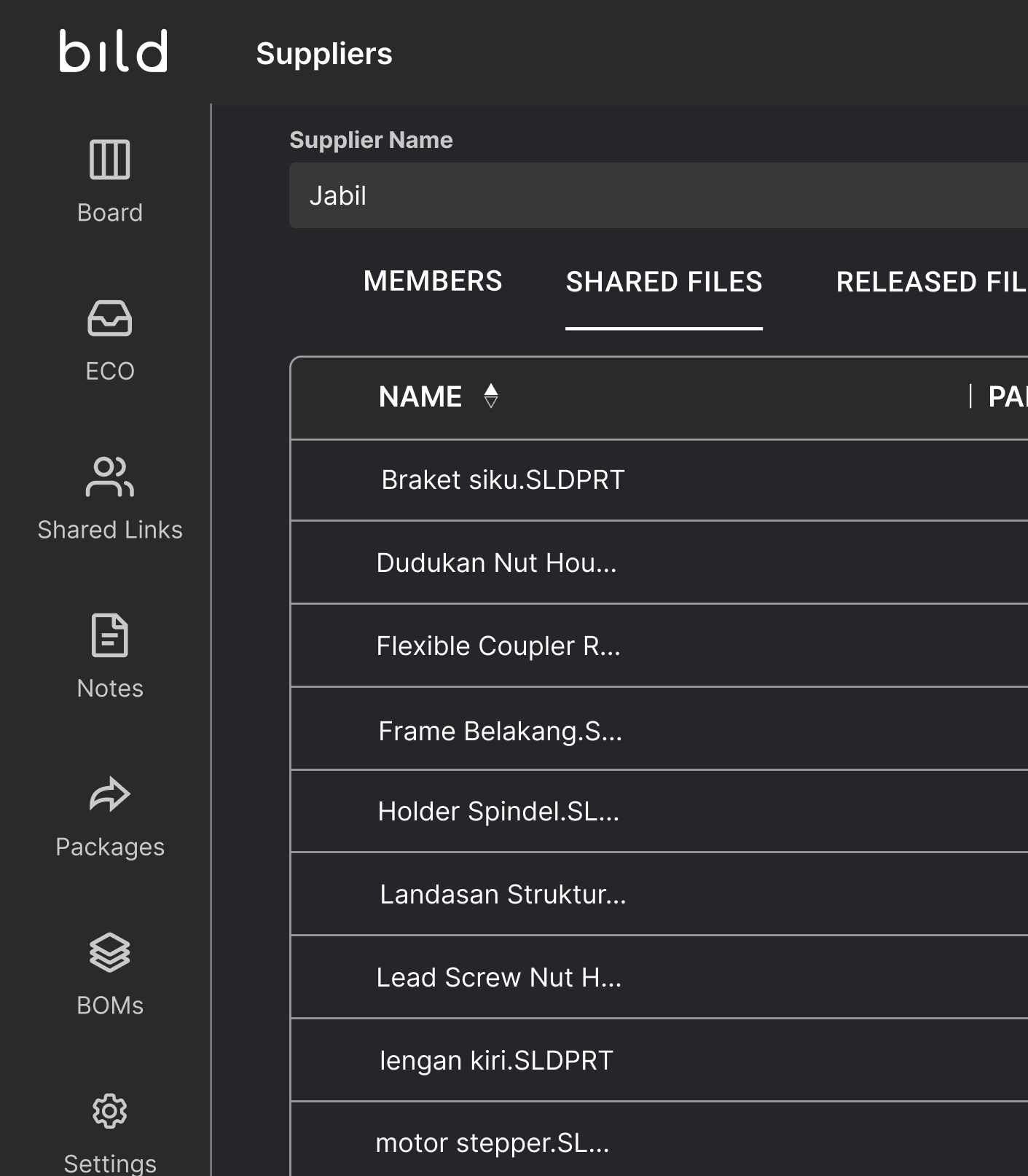
Suppliers receive information they are shared, and can share documentation back
Suppliers only see data they share, creating walls between suppliers
Easily see which designs are being shared to a specific supplier and which suppliers have access to a specific design
Add and manage alternate suppliers
Empowering teams to build smarter, faster, and together.






Any file from your vault can be shared, including CAD files, drawings, PDFs, or other documentation. Additionally, you have control over whether they can only view the file in our built-in viewer or if they have the ability to download the native or universal formats. You can also choose to share the latest version or only the latest released version of a file.
Yes. You can delete files from the Supplier Portal at any time to remove access to a design. You can also modify their permission to download native and universal formats at any point.
Yes. The Supplier Portal is a two-way portal where suppliers can share files back directly.
Yes. Suppliers cannot see which other supplier groups exist in your Bild environment.
No. They do not need a license to view files. They can open the files you share directly in our built-in 3D viewer. They will be able to explode assemblies, take measurements, and view cross-sections.